My First Week of CISSP Prep – What I’ve Learned So Far
I’ve survived my first week of CISSP prep. What did I learn? Before diving into the domains, I had to revisit the one concept everything else builds on. Let’s take a look.
Introduction
I just kicked off my CISSP preparation journey, and I wanted to share my first impressions and key takeaways. If you missed my introductory post about why I’m doing this and how I’m planning to approach it, you can check it out here.
How did I start?
I have started as I always do — from the basics. The fundamental cybersecurity concepts and terms.
According to my LinkedIn, I’m a Cybersecurity Manager. I have a degree in Cybersecurity. So why am I going back to the basics?
The answer is simple: because I believe mastering the basics is what separates good from great. Over the years, I’ve learned that without a crystal clear understanding of core principles, the more advanced stuff quickly falls apart.
In fact, when someone says "we can skip the intro, I know all this," I brace myself, because experience tells me that conversation is about to get..exhausting..
With that in mind, let’s start where it all begins:
The CIA Triad.
CIA Triad
The goal of Cybersecurity is the protection of information systems.
You wouldn’t have guessed that, right?
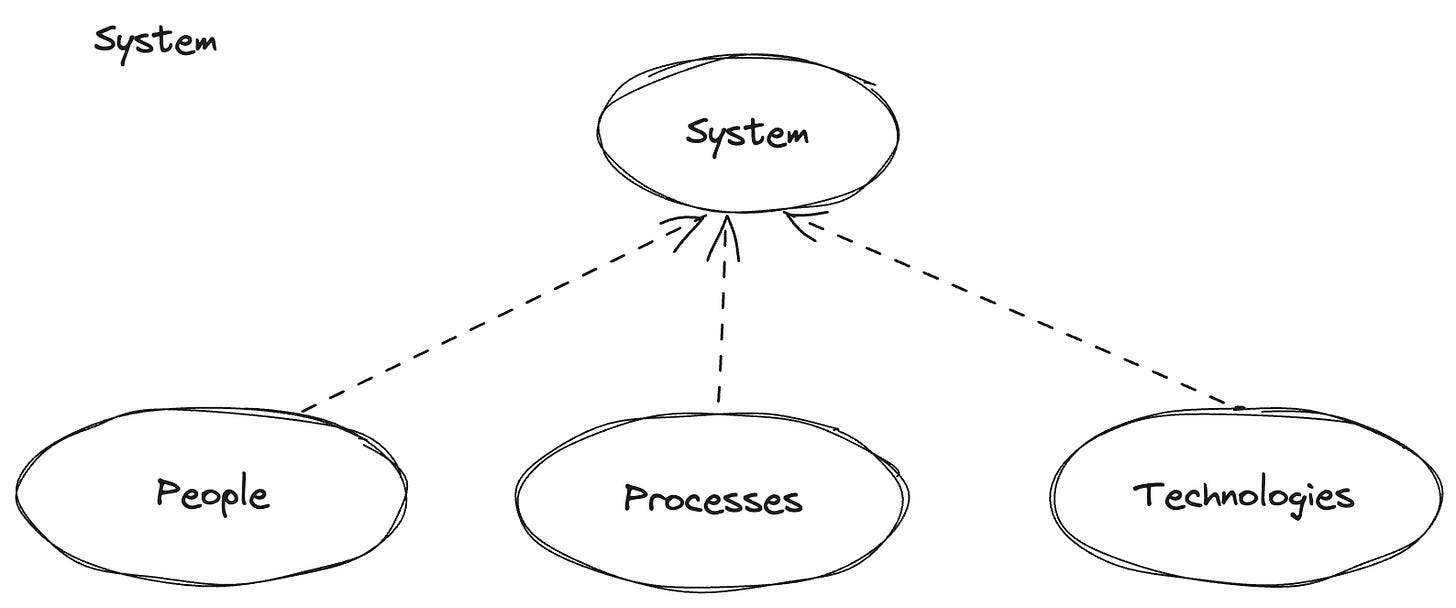
First, what exactly is an information system?
Spoiler: it’s not just a bunch of routers, servers, and laptops. It includes people and processes, too. And we, as CS specialists, need to handle all parts of the system. So, if you believe Cybersecurity is just about setting up firewalls and searching for vulnerabilities in the code, that ends today.
Now let’s break down the idea of "protection."
What does it actually mean to protect an information system? How would you define it? Should a security guard stand in front of the door to our server room? Or should we set up a firewall? Or should we keep our Windows up to date? Or should we encrypt all of our data?
There are so many options, right?
Well, not really. These are all valid actions, but they’re just controls. And if you implement any security control, you should understand why and what you are trying to achieve with it.
That’s where the CIA Triad comes in.
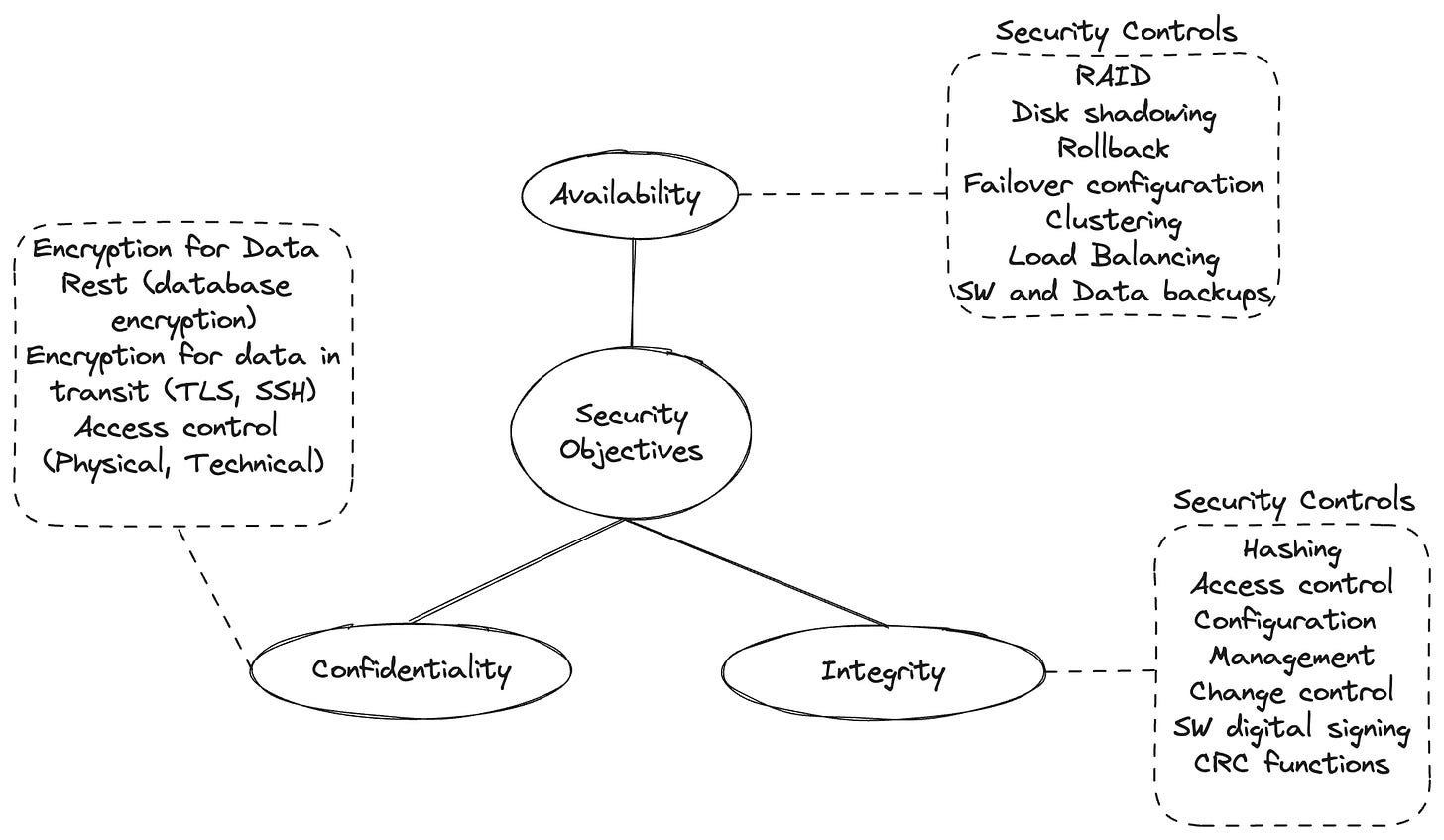
The CIA Triad defines the three core objectives of information security:
Confidentiality – making sure information is only accessible to those who are authorized.
Integrity – ensuring that data hasn’t been tampered with or altered without permission.
Availability – making sure systems and data are accessible when needed.
Protecting information systems means ensuring the CIA (Confidentiality, Integrity, Availability) of all assets in our information systems.
Every control, every policy, every process — it all comes back to supporting one or more of these three pillars.
So next time you hear “encrypt this file” or “install that patch,” stop and ask:
Which part of the CIA Triad are we actually supporting here?
Key takeaways
Most people skip the basics because of their ego, and then don’t fully understand the advanced concepts
CIA Triad isn’t just an acronym to memorize. It’s a way of thinking.
An objective isn’t a security control. Security controls only exist to support security objectives.
Every security decision must support one or more core objectives.
Knowing “what” isn’t enough — you need to know “why.”
One picture is more than 1,000 words
Curious what you'd add — or what helped you internalize these concepts? Let me know.
Study tips
I used flashcards to test myself on definitions and rewrote them in my own words.
Mind maps are a great way to visualize the connection between the definitions and terms
What’s Next
In the next post, we’ll continue building on this foundation, exploring how these core ideas connect across domains and decisions.
If you're interested in following my journey (or just want to steal a few insights for your own CISSP prep), feel free to subscribe — I’d love to have you onboard.