What does CEO have to do with cybersecurity, and who CPO even is?
Week 3 of my CISSP journey just finished and it’s time for me to sum it up. I moved from basic terms such as vulnerability or threat to roles and their responsibilities. Let’s find out how it works!
Ever confused by all those abbreviations? CEO, CFO, CIO, CPO, CSO…
You know those people are important, but do you know what they do?
Or what do the letters even stand for?
👉 Let me know in the comments if you can name all of them before reading further.
So, why do we even talk about them?
Because responsibilities in the organization are a huge part of cybersecurity.
If we can’t assign a responsibility to a specific role, and the role to a specific person, then it’s nearly impossible to secure the organizational systems.
Have you ever been in a situation where taking the trash out was no one’s responsibility?
If you haven’t, let me tell you what happens. Everybody is avoiding it for as long as possible.
But before we dive into specific roles and responsibilities, let’s define what a role even is.
So what exactly is a role?
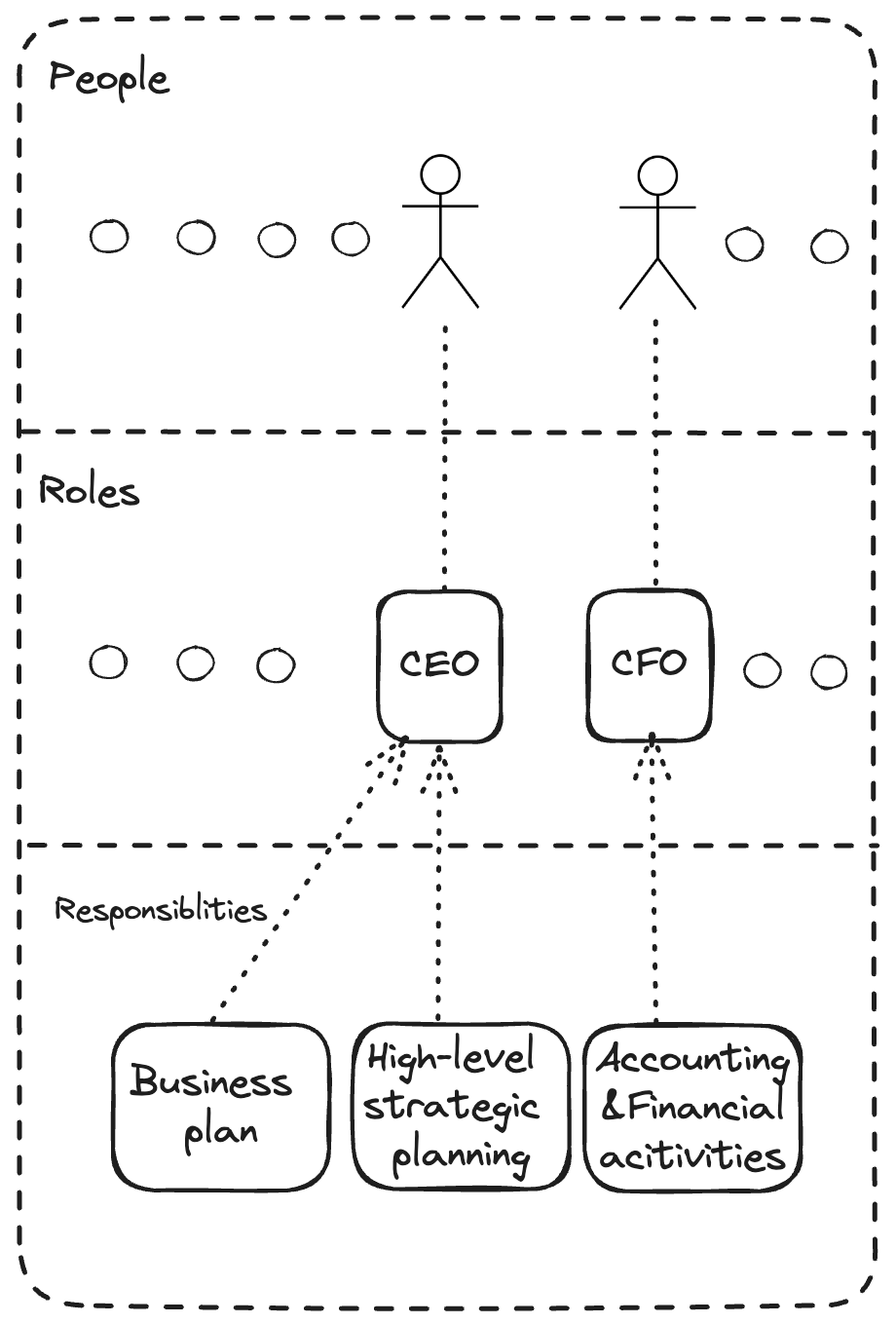
A role is a defined set of responsibilities within an organization, independent of who holds the position.
Think of it like a job description without a name attached.
And remember: one person can hold multiple roles. However, it isn’t common for C-suite roles such as CEO, CFO..
Why Don’t We Just Assign Specific Responsibilities to People?
Because with responsibility comes the need for:
Competence — Does the person know how to do it?
Authority — Are they allowed to make decisions?
Accountability — Can they be held responsible?
Roles ensure these things are structured, documented, and repeatable, no matter who comes and goes.
A role is a defined set of responsibilities that exists independently of the person assigned to it.
Important roles in large organizations
Now we know how to define a role, we should describe the most important roles for Cybersecurity. Because it doesn’t end at CISO and CSO.
C-Suite Roles & Cybersecurity Responsibilities
Chief Executive Officer (CEO): Ultimately responsible for the entire organization, including its security posture. Sets the tone at the top and ensures security is prioritized at the strategic level. (Responsible for the whole company)
Chief Financial Officer (CFO): Oversees budgeting and financial risk. Plays a key role in funding security initiatives and understanding the financial impact of security breaches.
Chief Information Officer (CIO): Responsible for the organization’s overall IT strategy and infrastructure. Collaborates with security leaders to ensure systems are secure by design.
Chief Privacy Officer (CPO): Focuses on compliance with privacy regulations (e.g. GDPR). Works closely with cybersecurity teams to ensure personal data is properly handled and protected.
Chief Security Officer (CSO): The CSO is responsible for understanding the risks that the company faces and for mitigating them to an acceptable level.
Chief Information Security Officer (CISO):
Leads the cybersecurity program. Defines security strategy, policies, and risk management practices. Acts as the bridge between technical teams and executive leadership.
👀 In the next article, I’ll dive into the differences between the CISO and CSO. These roles that are often confused but serve slightly different functions.
Key Security & Operational Roles
Data Owner
Accountable for data classification, access decisions, and usage policies. Defines who can access what, and under what circumstances.
Data Custodian
Implements controls defined by the Data Owner. Manages the technical storage, transmission, and backup of data.
System Owner
Responsible for the operation and maintenance of specific systems. Ensures systems are secure, patched, and compliant.
Data Analyst
Responsible for ensuring that data is stored in a way that makes the most sense to the company and to the individuals who need to access it.
User (End-User)
All employees, contractors, or third parties accessing organizational systems. Expected to follow security policies and undergo regular awareness training.
Auditor
Independently reviews security controls and practices. Provides assurance to stakeholders that the organization is following policy and regulatory requirements.
Why This All Matters
Let’s be real — most companies don’t have every single one of these roles filled.
But the responsibilities still exist.
And if they’re not clearly assigned, they become no one’s responsibility, which is often the perfect setup for a security breach.
That’s why security frameworks introduce roles and responsibilities. Because without a clear structure and hierarchy, there’s no accountability..
It’s about creating clarity within your organization, especially when it comes to security.
Cybersecurity isn’t just the responsibility of the IT department or the CISO. It’s everyone’s responsibility, from senior management to operational staff.
Whether you're making strategic decisions, managing systems, or simply clicking links in emails, every role plays a part in protecting the organization.
Security only works when everyone does their part.
Final Thoughts
If you're preparing for the CISSP or just working in cybersecurity, a clear understanding of these roles is essential.
Every control, every process, every incident response plan depends on people who know what they're responsible for.
Let me know what roles your company has, or doesn’t have.
And if you want me to turn this into a cheat sheet or infographic, just say the word.
✍️ This post is part of my weekly CISSP journey series. I write, share study notes, and reflect on what I’m learning.
🔐 If you're enjoying these breakdowns, consider subscribing, and feel free to share this post with your team or study group.



!! CISSP Roles & Responsibilities Quiz !!
Now it's time to test how much I’ve actually learned.
Want to play along?
Let’s go.👇
https://forms.gle/rzZPyvmZxrWGX5PC8