Hashing algorithms: What any Cybersecurity specialist needs to know about them
Understanding why hashing is so important is crucial for any cybersecurity specialist. After all, it is how we achieve data integrity, which is one of the core goals of cybersecurity.
Hello everyone! 👋
Hashing is one of the key mechanisms in Cybersecurity that helps us achieve one of the core goals of Cybersecurity: Integrity.
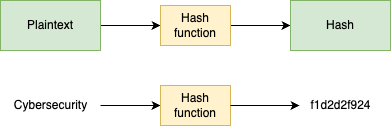
As you already know, hashing is a one-way process that transforms data into a fixed-length output called a hash or digest.
What Is a Hashing Algorithm?
Definition: A hashing algorithm is a mathematical function that takes an input and produces a hash.
I can imagine you might be a bit confused right now.
You’re probably thinking: “That’s it? Just a function that takes an input and spits out an output?”
And honestly, you’re right!
Creating a simple function that takes any input and produces a fixed-length output is easy. You could create one in under 5 minutes.
But that’s not where the story ends.
Let’s take a look at what makes a hashing function secure.
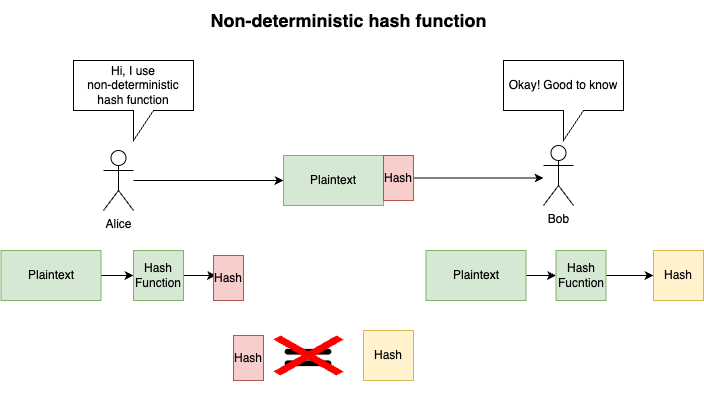
Deterministic: The same input always gives the same output.
If the hash function isn’t deterministic, it would be completely useless for verifying integrity of data. Same input, no changes, different hash. You can see the problem, right?Fast to compute: Efficient processing, even for large data.
Efficiency is key, especially when hashing things like software updates or massive databases.Collision-resistant: Hard to find two inputs with the same hash.
If a function isn’t collision-resistant, an attacker could tamper with the data while keeping the same hash. That would completely break its purpose.Pre-image resistant: You can’t reverse a hash to find the original input.
If you could, passwords and sensitive data would be at risk even if only the hashes were exposed.Avalanche effect: A small change in input drastically changes the hash.
This ensures that even small alterations in data (like a single character) are immediately obvious.
Well-Known Hashing Algorithms
1. MD5 (No longer considered secure)
Originally popular for its speed and simplicity, MD5 is now considered broken due to known vulnerabilities. It's susceptible to collisions, meaning two different inputs can produce the same hash.
2. SHA-1 (No longer considered secure)
An improvement over MD5, but still not secure today. It’s also vulnerable to collision attacks and should be avoided in modern applications.
3. SHA-256
Part of the SHA-2 family, this is one of the most widely used and secure hashing algorithms today. It’s used in everything from digital signatures to blockchain technologies.
4. SHA-3
The latest member of the Secure Hash Algorithm family. Designed to be resilient against emerging threats, SHA-3 offers an alternative to SHA-2 with a completely different structure and stronger theoretical guarantees.
Conclusion
Understanding why hashing is so important is crucial for any Cybersecurity specialist. After all, it is one of the most commonly used ways of achieving data integrity, which is, in many cases, more important than confidentiality. If you’re considering passing any Cybersecurity exams, such as CC from ISC2, you will need to understand how and when hashing is used and what the key features of any secure hashing function are. So make sure to subscribe to my Patreon for free to find out more about hashing and other Cybersecurity concepts!
📩 Subscribe to my Patreon for free so you won’t miss the next posts — especially if you’re just starting your journey into cybersecurity!
📘 Glossary – 10 Key Terms
Hash – Fixed-length output generated by a hashing algorithm.
Hashing Algorithm – Function that converts data into a hash.
Deterministic – Same input always results in the same hash.
Collision – When two different inputs produce the same hash.
Pre-image Resistance – Hard to reverse a hash to original data.
Avalanche Effect – Tiny input change = drastically different hash.
MD5 – Outdated, insecure hash algorithm vulnerable to collisions.
SHA-1 – Better than MD5, but also considered broken.
SHA-256 – Secure, modern hash used in blockchain and beyond.
SHA-3 – Latest standard with strong resistance to new threats.